Never trust, always verify

Organizations advancing their cybersecurity maturity are building an actionable roadmap that identifies ways to reduce their attack surface, detect and respond to cyber threats, and implement ways to recover from cyber attacks, all with Zero Trust enabling capabilities.

Zero Trust isn’t a single solution or piece of hardware. It’s a set of principles that governs the way we approach federal cybersecurity. The intended outcome of a Zero Trust model is for trusted identities to get access to the applications, systems, networks, and data based on their roles and what they need to perform their jobs.
Wilflower International, along with Dell Technologies and our other trusted partners, work closely to support our nation’s government agencies and the Department of Energy. We bring together the expertise and end-to-end intelligent solutions to help you simply, securely and responsibly innovate and collaborate to deliver data-driven breakthrough experiences for your customers and your workforce, no matter where the mission takes them.
The Dell Technologies approach to Zero Trust is based on integrating the seven tenets outlined in a National Institute Standards and Technology (NIST) Special Publication 800- 207 as well as seven pillars of the Department of Defense’s Zero Trust reference architecture.
Device trust
User trust
Transport and session trust
Application trust
Data trust
Visibility: Dashboards, logging alerts, Inventory submission, data tagging, metadata
Analytics: trend graphing, traffic reporting, data utilization reporting, etc.
Orchestration: Policy engines, base line configuration definition
Automation: Automated remediation engines, conditional access, mechanisms, incident response playbooks
Dell Technologies brings a secure supply chain and built-in cyber resiliency to all of our products and solutions. We also offer a broad range of specialized security solutions to counter cyberthreats and minimize attacks that compromise sensitive data and citizen information.
Long before Zero Trust became an industry catchphrase, Dell Technologies products, like the next-generation PowerMax storage, employed Zero Trust principles. The intrinsic security capabilities of our compute and storage products map directly Zero Trust functions. These capabilities include PIV/CAC authentication, encryption at rest and in transit, and telemetry data for real-time monitoring. You can install as many security tools and solutions on top of servers as you want, but if the underlying hardware and firmware can’t be trusted, then your security investments could potentially to go waste.
Define targets
What are key properties?

Current state
How are you operating today, and
are you leveraging assets effectively?
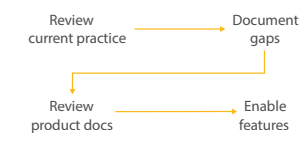
Adapt/adopt
Modernize network, architecture and
applications to address remaining gaps.
There is no single product or process change that can address all Zero Trust initiatives; however, by defining your targets, understanding current operations, and adapting to new processes, you can address individual gaps with innovative Zero Trust architectures. Dell Federal Cybersecurity Advisory Services can help assess where you align with recent federal mandates, and help you develop a roadmap to achieve your Zero Trust goals.
There are multiple capabilities within and spread across the Zero Trust pillars, and a complete solution requires products from several vendors. Dell Technologies works with its extensive partner ecosystem to engineer comprehensive Zero Trust outcomes like identity management, endpoint compliance, Zero Trust networking, and IA/ML data analytics. Our strong security foundation across our portfolio coupled with being one of the most trusted technology integrators in the world, makes Dell Technologies a great choice for assisting our federal customers in their Zero Trust journeys.
The federal civilian Zero Trust strategy (OMB M-22-09) and the DOD Zero Trust strategy are requiring government organizations to rapidly deploy the new security paradigm. Dell Technologies is working closely with the Federal System Integrators and architected outcome-based Zero Trust solutions that are used in the US Government today. To further support our federal customers, Dell is building a Zero Trust Center of Excellence for testing workloads and exploring the intricacies of a Zero Trust environment.

Organizations advancing their cybersecurity maturity are building an actionable roadmap that identifies ways to reduce their attack surface, detect and respond to cyber threats, and implement ways to recover from cyber attacks, all with Zero Trust enabling capabilities.
© Wildflower Int’l. LTD. Copyright all rights reserved.